Microsoft is making security defaults available to everyone because managing security can be difficult. Identity-related attacks like password spray, replay, and phishing are common in today’s environment. More than 99.9% of these identity-related attacks are stopped by using Multi-Factor Authentication (MFA) and blocking legacy authentication. The goal is to ensure that all organizations have at least a basic level of security enabled at no extra cost.
The steps to configure security settings are as follows:
a. Enable Azure Active Directory Security Defaults
Azure Active Directory (Azure AD) is a cloud-based identity and access management service. This service helps your employees access external resources, such as Microsoft 365, the Azure portal, and thousands of other SaaS applications. Azure Active Directory also helps them access internal resources like apps on your corporate intranet network, along with any cloud apps developed for your own organization.
Here are the ways to enable security defaults in your directory:
- Sign-in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
- Browse to Azure Active Directory > Properties.
- Select Manage security defaults.
- Set the Enable security defaults toggle to Yes.
- Select Save.
After enable the security defaults, you must enforce the security policies:
- Require all users to register for Azure AD Multi-Factor Authentication
- Require administrators to do Multi-Factor Authentication
- Require users to do Multi-Factor Authentication when necessary
- Block legacy authentication protocols
- Protect privileged activities like access to the Azure portal
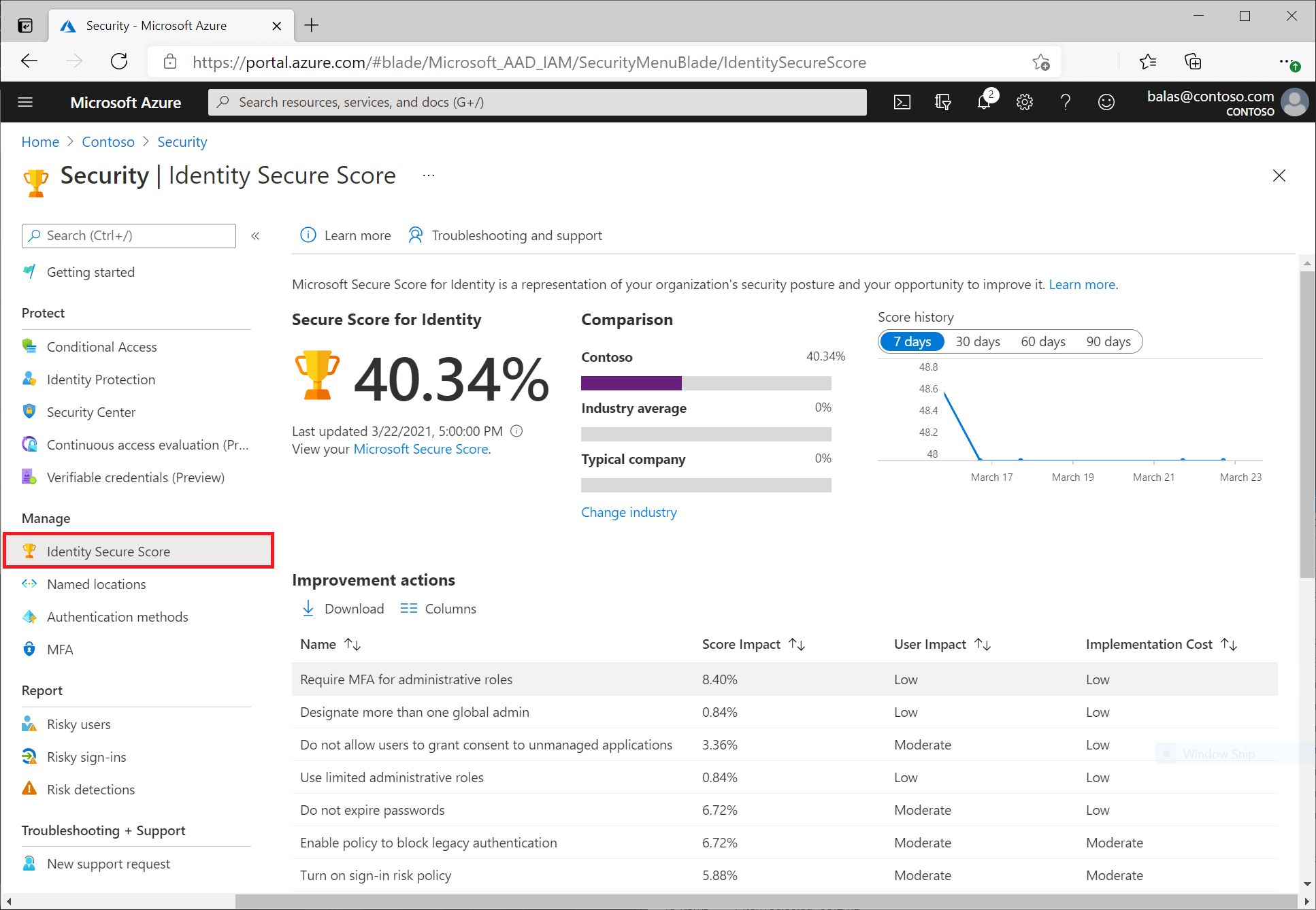
b. Check and Improve Your Identity Secure Score
The identity secure score is percentage that functions as an indicator for how aligned you are with Microsoft’s best practice recommendations for security. Each improvement action in identity secure score is tailored to your specific configuration.
You can access the score and related information on the identity secure score dashboard. On this dashboard, you find:
- A comparison graph showing how your Identity secure score compares to other tenants in the same industry and similar size
- A trend graph showing how your Identity secure score has changed over time
- A list of possible improvements
The secure score helps you to:
- Objectively measure your identity security posture
- Plan identity security improvements
- Review the success of your improvements
c. Review Best Practices for Azure AD Roles
- Manage to least privilege
Least privilege means you grant your administrators exactly the permission they need to do their job. There are three aspects to consider when you assign a role to your administrators: a specific set of permissions, over a specific scope, for a specific period of time.
- Use Privileged Identity Management to grant just-in-time access
Azure AD Privileged Identity Management (PIM) lets you grant just-in-time access to your administrators. Microsoft recommends that you enable PIM in Azure AD. Using PIM, a user can be made an eligible member of an Azure AD role where they can then activate the role for a limited time when needed.
- Turn on Multi-Factor Authentication for all your administrator accounts
You can enable MFA on Azure AD roles using two methods:
- Role settings in Privileged Identity Management
- Conditional Access
- Configure recurring access reviews to revoke unneeded permissions over time
Access reviews enable organizations to review administrator’s access regularly to make sure only the right people have continued access.
- Limit the number of Global Administrators to less than 5
As a best practice, Microsoft recommends that you assign the Global Administrator role to fewer than five people in your organization. By default, when a user signs up for a Microsoft cloud service, an Azure AD tenant is created, and the user is made a member of the Global Administrators role. Users who are assigned the Global Administrator role can read and modify every administrative setting in your Azure AD organization.
- Use groups for Azure AD role assignments and delegate the role assignment
You can assign an owner to role-assignable groups. That owner decides who is added to or removed from the group, so indirectly, decides who gets the role assignment. In this way, a Global Administrator or Privileged Role Administrator can delegate role management on a per-role basis by using groups.
- Activate multiple roles at once using privileged access groups
Create a privileged access group and grant it permanent access to multiple roles (Azure AD and/or Azure). Make that user an eligible member or owner of this group. With just one activation, they will have access to all the linked resources.
- Use cloud native accounts for Azure AD roles
Avoid using on-premises synced accounts for Azure AD role assignments. If your on-premises account is compromised, it can compromise your Azure AD resources as well.
d. Consider Azure Active Directory Passwordless Sign-In
Features like Multi-Factor Authentication (MFA) are a great way to secure your organization, but users often get frustrated with the additional security layer on top of having to remember their passwords. Passwordless authentication methods are more convenient because the password is removed and replaced with something you have, plus something you are or something you know.
Here are some factors for you to consider when choosing Microsoft passwordless technology:
Find Out More!
If you would like to find out more about Technosoft Business Solution, please do not hesitate to contact us:
- Sales, PT Graha Technosoft Informatika, 62-21-5658566, sales@technosoft.co.id
- Info, PT Graha Technosoft Informatika, 62-21-565-8566, info@technosoft.co.id
Sources:
- https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
- https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/identity-secure-score
- https://docs.microsoft.com/en-us/azure/active-directory/roles/best-practices
- https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-passwordless